2. Composition of the Guidebook
2.1. Developer’s Context
Many guidebooks that have been written on secure coding include warnings about harmful coding practices and their suggested revisions. Although this approach can be useful at the time of reviewing the source code that has already been coded, it can be confusing for developers that are about to start coding, as they do not know which article to refer to.
The Guidebook has focused on the developer’s context of “What is a developer trying to do at this moment?” Equally, we have taken steps to prepare articles that are aligned with the developer’s context. For example, we have divided articles into project units by presuming that a developer will be involved in operations such as "Creating/Using Activities", "Using SQLite", etc.
We believe that by publishing articles that support the developer’s context, developers will be able to easily locate necessary articles that will be instantly useful in their projects.
2.2. Sample Code, Rule Book, Advanced Topics
Each article is made up of three sections: Sample Code, Rulebook, and Advanced. If you are in a hurry, please refer to the Sample Code and Rulebook. The content is broken down into reusable patterns to a certain extent. If you have issues that do not fit into the Sample Code and Rulebook sections, please refer to the Advanced section. It contains materials to consider when considering how to solve individual issues.
Unless otherwise noted, the sample code and article content are intended for Android 7.0 (API Level 24) and later. Please note that operation has not been confirmed for versions earlier than Android 7.0 (API Level 24), and the countermeasures may not be effective. Also, even if the version is within the target range, please verify operation on the device where it is installed and use it at your own risk.
Additionally, starting with Android 14 and Android 15, there are minimum targetSdkVersion requirements for apps that can be installed, which aims to prevent malware from targeting older API levels to circumvent newer security protections and eliminate such malware across the board.
The targetSdkVersion that can be installed for each Android version is as follows:
Android Version |
Installable targetSdkVersion |
|---|---|
Android 7.0~13 |
No restrictions |
Android 14 |
targetSdkVersion 23 or later |
Android 15~ |
targetSdkVersion 24 or later |
2.2.1. Sample Code
Sample code that serves as the basic model within the developer's context and functions as the theme of an article is published in the Sample Code section. If there are multiple patterns, we have provided source code for the different patterns and classified them accordingly. We have strived to make our commentaries as simple as possible. For example, when we want to direct the reader's attention to a security issue that requires attention, a bullet-point number will appear next to "Point" in the article. We will also comment on the sample code that corresponds to the bullet-point number by writing "*** Point (Number) ***." Please note that a single point may correspond to multiple pieces of sample code. There are sections throughout the entire source code, albeit very little compared to the entire code, which requires our attention for security. In order to be able to survey the sections that call for scrutiny, we try to post the entire class unit of sample code.
Please note that only a portion of sample code is posted in the Guidebook. A compressed file, which contains the entire sample code, is made public in the URL listed below. It is made public by the Apache License, Version 2.0; therefore, please feel free to copy and paste it. Please note that we have minimized the code for error processing in the sample code to prevent it from becoming too long.
https://www.jssec.org/dl/android_securecoding_en.zip Sample Codes Archive
The projects/keystore file that is attached in the sample code is the keystore file that contains the developer key for the signature of the APK. The password is "android." Please use it when singing the APK in the In-house sample code.
We have provided the keystore file, debug.keystore, for debugging purposes. When using Android Studio for development, it is convenient for verifying the operational capability of the In-house sample code if the keystore is set for each project. In addition, for sample code that is comprised of multiple APKs, it is necessary to match the android:debuggable setting contained inside each AndroidManifest.xml in order to verify the cooperation between each APK. If the android:debuggable setting is not explicit set when installing the APK from Android Studio, it will automatically become android:debuggable= "true."
For embedding the sample code as well as keystore file into Android Studio, please refer to "2.5. Importing Sample Code into Android Studio".
2.2.2. Rule Book
Rules and matters that need to be considered regarding security within the developer's context will be published in the Rule Book section. Rules to be handled in that section will be listed in a table format at the beginning and will be divided into two levels: "Required" and "Recommended." The rules will consist of two types of affirmative and negative statements. For example, an affirmative statement that expresses that a rule is required will say "Required." An affirmative statement that expresses a recommendation will say "Recommended." For a negative statement that expresses the requisite nature of the rule would say, "Definitely not do." For a negative sentence that expresses a recommendation would say, "Not recommended." Since these differentiations of levels are based on the subjective viewpoint of the author, it should only be used as a point of reference.
Sample code that is posted in the Sample Code section reflect these rules and matters that need to be considered, and a detailed explanation on them is available in the Rule Book section. Furthermore, rules and matters that need to be considered that are not dealt with in the Sample Code section are handled in the Rule Book section.
2.2.3. Advanced Topics
Items that require our attention, but that could not be covered in the Sample Code and Rule Book sections within the developer's context will be published in the Advanced Topics section. The Advanced Topics section can be utilized to explore ways to solve separate issues that could not be solved in the Sample Code or Rule Book sections. For example, subject matters that contain personal opinions as well as topics on the limitations of Android OS in relation the developer's context will be covered in the Advanced Topics section.
Developers are always busy. Many developers are expected to have basic knowledge of security and produce many Android applications as quickly as possible in a somewhat safe manner rather than to really understand the deep security matters. However, there are certain applications out there that require a high level of security design and implementation from the beginning. For developers of such applications, it is necessary for them to have a deep understanding concerning the security of Android OS.
In order to benefit both developers who emphasize development speed and also those who emphasize security, all articles of the Guidebook are divided into the three sections of Sample Code, Rule Book, and Advanced Topics. The aim of the Sample Code and Rule Book sections is to provide generalizations about security that anyone can benefit from and source code that will work with a minimal amount of customization and hopefully by just copying and pasting. In the Advanced Topics section, we offer materials that will help developers think in a certain way when they are facing specific problems. It is the aim of the Advanced Topics section to help developers examine optimal secure design and coding when they are involved in building individual applications.
2.3. The Scope of the Guidebook
The purpose of the Guidebook is to collect security best practices that are necessary for general Android application developers. Consequently, our scope is focused mainly on security tips (The "Application Security" section in figure below) for the development of Android applications that are distributed primarily in a public market.
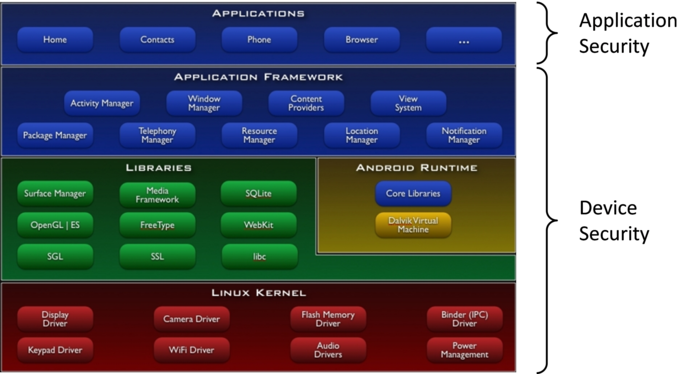
Fig. 2.3.1 Main Components of the Android Platform
Security regarding the implementation of components in the "Device Security" of the above figure is outside the scope of this guidebook. There are differences in the viewpoint of security between general applications that are installed by users and pre-installed applications by device manufacturers. The Guidebook only handles the former and does not deal with the latter. In the current version, tips only on the implementation by Java are posted, but in future versions, we plan on posting tips on JNI implementations as well.
Also as of now we do not handle threats that results from an attacker obtaining root privileges. We will assume the premise of a secure Android device in which it is not possible to obtain root privileges and base our security advice on utilizing the Android OS security model. For handling of assets and threats, we have provided a detailed description on "3.1.3. Asset Classification and Protective Countermeasures."
2.4. Literature on Android Secure Coding
Since we are not able to discuss all of Android's secure coding in the Guidebook, we recommend that you read the literature mentioned below in conjunction with the Guidebook.
Android Security: Anzenna Application Wo Sakusei Surutameni (Secured Programming in Android)Author: Tao Software Co., Ltd. ISBN: 978-4-8443-3134-6The CERT Oracle Secure Coding Standard for JavaAuthors: Fred Long, Dhruv Mohindra, Robert C. Seacord, Dean F.Sutherland, David SvobodaOWASP Mobile Application Security Verification Standard (MASVS)Author: The OWASP FoundationOWASP Top 10Author: The OWASP Foundation10 Major Checkpoints for Mobile Application Development 2023Author: JSSEC Technical Subcommittee, 10 Major Checkpoints for Mobile Application Development 2023 Selection Committee
2.5. Importing Sample Code into Android Studio
This section explains the procedure for importing sample code into Android Studio. The sample code is divided into multiple projects according to their purpose. The method for importing these projects is described in 2.5.1. Importing Sample Projects.
2.5.1. Importing Sample Projects
2.5.1.1. Download the Sample Code
Obtain the sample code from the URL introduced in 2.2.1. Sample Code.
2.5.1.2. Extract the Sample Code
Right-click the sample code compressed in a Zip file, then click “Extract All” from the displayed menu.
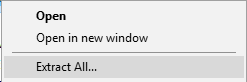
Fig. 2.5.1 Extracting the Sample Code
2.5.1.3. Specify the Extraction Destination
Here, a workspace named “C:android_securecoding” will be created. Specify “C:” and click the “Extract” button.
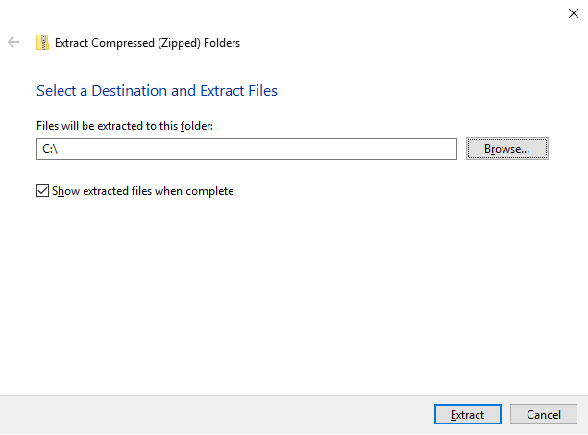
Fig. 2.5.2 Specifying the Extraction Destination
When you click the “Extract” button, a folder named “android_securecoding” will be created directly under “C:”.
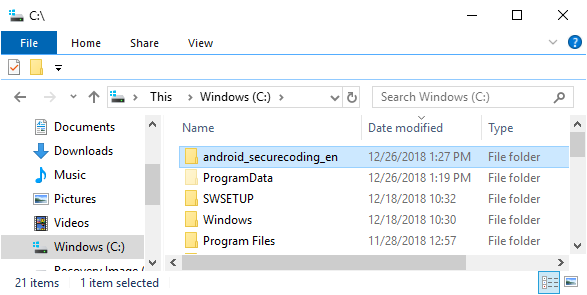
Fig. 2.5.3 android_securecoding Folder
The “android_securecoding” folder contains the sample code.
For example, if you want to refer to the sample code for 4.1.1.4. Creating/Using In-house Activities in 4.1. Creating/Using Activities please look here:
android_securecoding
┗ Create Use Activity
┗ Activity InhouseActivity
As shown above, the “android_securecoding” folder contains subfolders for each chapter where sample code projects are arranged accordingly.
2.5.1.4. Build the Sample Code
Start Android Studio from the Start menu or desktop icon.
Fig. 2.5.4 Starting Android Studio
Click “Open.”
Fig. 2.5.5 Clicking Open
Select the project folder to open.
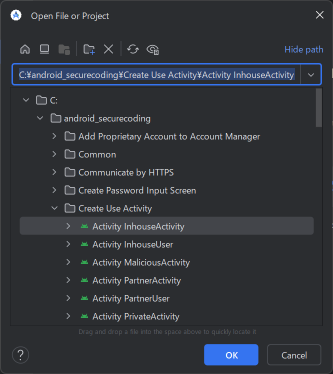
Fig. 2.5.6 Selecting the Project Folder
The project will open.
Fig. 2.5.7 Project Opened
To run the app created from the sample code on an Android device or emulator, signing is required. Set the debug key file “debug.keystore” used for signing in the Android Studio project.
Click File -> Project Structure…
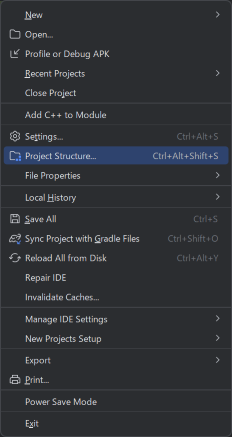
Fig. 2.5.8 File -> Project Structure
Select “debug.keystore” as the Store File and click OK.
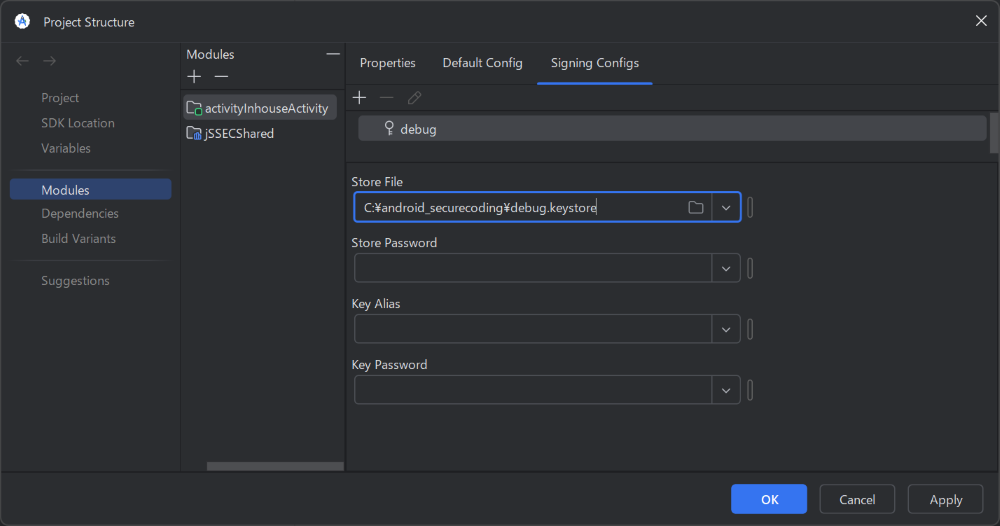
Fig. 2.5.9 Selecting debug.keystore
Click Build -> Make Project…
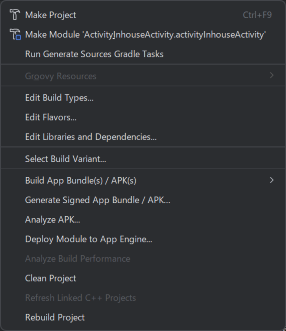
Fig. 2.5.10 Clicking Make Project